The Microsoft Identity and Access Administrator certification or SC-200 training focuses on designing, implementing, and managing identity solutions that securely connect users to applications, resources, and services. It covers core Microsoft Entra ID capabilities like authentication, authorization, identity governance, conditional access, privileged identity management, and integrating on-premises and cloud identity systems. This role ensures users have the right access at the right time while safeguarding organizational data and compliance.
Microsoft Sentinel training is on cloud-native SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) platform built on Azure. It collects, correlates, and analyzes security data from across an organization’s digital estate—on-premises, cloud, and hybrid environments—using analytics rules, machine learning, and threat intelligence. Sentinel enables real-time threat detection, automated incident response through playbooks, and deep investigation capabilities with Kusto Query Language (KQL), helping security teams quickly identify, understand, and neutralize threats.
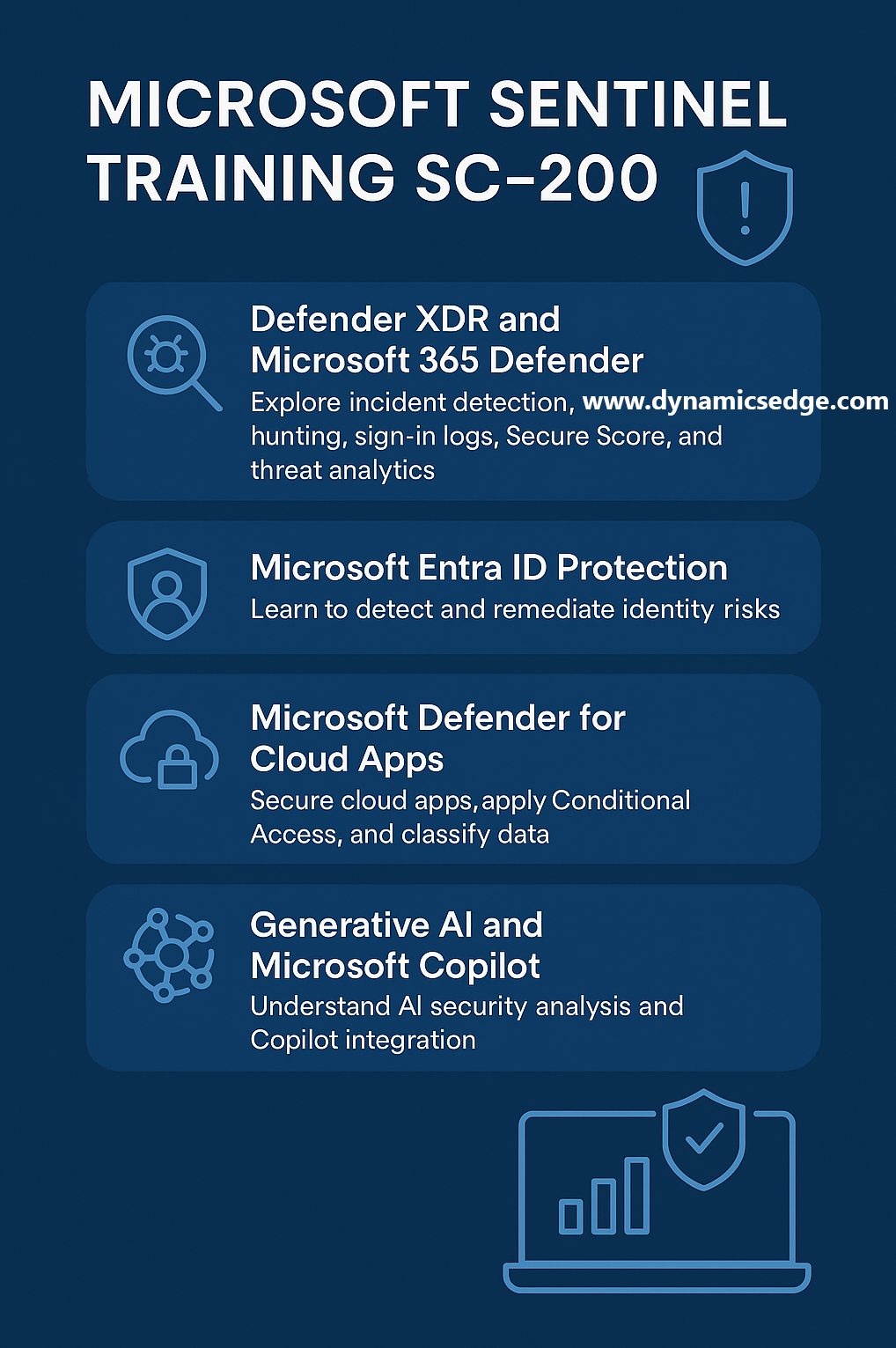
The SC-200 Microsoft Security Operations Analyst course provides a deep, practical foundation in using Microsoft’s security tools to investigate, respond to, and hunt for threats across enterprise environments. It begins by exploring Microsoft Defender XDR and its role within a Security Operations Center (SOC), showing how security incidents are detected, analyzed, and managed using Defender’s integrated threat protection suite. Early modules emphasize incident mitigation in Microsoft 365 Defender, including advanced hunting, Entra sign-in log analysis, and leveraging Secure Score and threat analytics to strengthen security posture. The program also covers identity risk detection and remediation with Microsoft Entra ID Protection, targeted threat protection in Microsoft Defender for Office 365, and account protection with Microsoft Defender for Identity. Learners also work through securing cloud apps with Microsoft Defender for Cloud Apps, applying Conditional Access App Control, classifying sensitive information, and detecting threats in cloud workloads.
The course expands into generative AI and Microsoft Copilot for Security, giving a solid understanding of AI-assisted security analysis, prompt creation, and Copilot integration across Defender XDR, Microsoft Purview, Entra, and Intune. This bridges into compliance and insider risk modules within Microsoft Purview, where learners respond to data loss prevention alerts, manage insider risk cases, configure notice templates, and conduct in-depth audit searches, including Copilot interaction auditing. Additional Purview content covers eDiscovery and content search for investigations, including targeted email message removal.
The focus then shifts to Microsoft Defender for Endpoint with a series of hands-on modules covering environment deployment, attack surface reduction, device investigations, live response sessions, evidence analysis, automation configuration, alert tuning, and vulnerability management. From there, the curriculum addresses cloud workload protection with Microsoft Defender for Cloud, showing how to connect Azure and non-Azure resources, monitor Secure Score, enforce regulatory compliance, and apply workload-specific protections for servers, storage, databases, containers, and more. Learners practice alert remediation, automation, and generating threat intelligence reports in Defender for Cloud.
A significant portion of the training is devoted to Microsoft Sentinel, starting with Kusto Query Language (KQL) fundamentals for detection, reporting, and threat hunting. This includes constructing, filtering, and summarizing queries, building multi-table joins, extracting structured and unstructured data, and creating parsers. Sentinel modules cover workspace management, data connectors for Microsoft and third-party sources, watchlists, threat intelligence integration, analytics rule creation, playbook automation, incident management, behavioral analytics, and data normalization with ASIM Parsers. Visualization and monitoring techniques are also taught through Sentinel Workbooks, along with structured threat hunting processes based on MITRE ATT&CK, bookmark usage, livestream monitoring, historical search jobs, and advanced hunting via notebooks.
By the end, learners have developed the ability to integrate, analyze, and respond across the entire Microsoft security stack—from identity and endpoint protection to cloud workloads and SIEM/SOAR operations—using advanced KQL, automation, and AI-assisted workflows to accelerate detection and remediation in real-world security operations.
Have a Question ?
Fill out this short form, one of our Experts will contact you soon.
Talk to an Expert Today
Call Now